RBAC
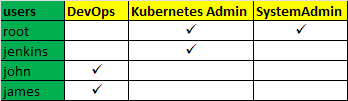
In this page, we will see the Kubernetes RBAC with real-time examples. I have three teams like below. But, our focus on this page is for the two new users(John and James) part of the DevOps team.
I will quickly touch base on some of the Kubernetes terminology, which we cover in the RBAC section.
In Kubernetes, there is no concept like user authentication through username and password. All authentication happens to the Kubernetes cluster via certificates or tokens. Access to the users can be done in two ways,
- Role & Role Binding - At namespace level access
- Cluster Role and Cluster Role Binding - At cluster level access
RBAC Architecture
In the above architecture, when the new user(John) needs access to any of the Kubernetes resources like pods, volumes, services etc, as a first thing the user should be authenticated first and then should be authorized based on the roles or the action that person should perform.
A) Authentication
1) System Admin(root user) - Centos 9
- sudo adduser john
- sudo passwd john
- sudo usermod -a -G wheel john
- mkdir /tmp/rbac // optional
- chown jenkins:jenkins /tmp/rbac //optional
2) Kubernetes admin - Logon to Kubernetes Cluster
In the below steps, we are creating a key to get into the cluster. Then you need to create a certificate signed request(csr). In Kubernetes, for any users to get access, that user has to establish trust with ca.key and ca.crt
- cd /tmp/rbac
- openssl genrsa -out john.key 2048
- openssl req -new -key john.key -out john.csr -subj "/CN=john/O=devops"
- sudo openssl x509 -req -in john.csr -CA /etc/kubernetes/pki/ca.crt -CAkey /etc/kubernetes/pki/ca.key -CAcreateserial -out john.crt -days 365
3) Create credentials for the user John as Kubernetes admin
- kubectl config --kubeconfig=john.kubeconfig set-cluster kubernetes --server=https://192.168.86.30:6443 --certificate-authority=/etc/kubernetes/pki/ca.crt
- kubectl config --kubeconfig=john.kubeconfig set-credentials john --client-certificate=john.crt --client-key=john.key
- kubectl config --kubeconfig=john.kubeconfig set-context john-kubernetes --cluster=kubernetes --namespace=devops --user=john
- chmod 777 john.kubeconfig
4) Set Context - As Kubernetes Admin
- kubectl config --kubeconfig=john.kubeconfig get-contexts
- kubectl config --kubeconfig=john.kubeconfig use-context john-kubernetes
5) Verification - Forbidden error expected (Login as John)
- kubectl --kubeconfig=john.kubeconfig get pods
B) Authorization
1) Create Role - As Kubernetes Admin
- kubectl create role devops --verb=get,list --resource=pods --namespace devops
- kubectl -n devops get role devops -o yaml
2) Create Role-Binding - As Kubernetes Admin
- kubectl create rolebinding devops-rolebinding --role=devops --user=john --namespace devops
- kubectl -n devops get rolebinding devops-rolebinding -o yaml
3) Verification - This time, it should work (Login as John)
- kubectl --kubeconfig=john.kubeconfig get pods
C) For multple users, the ideal way is to have a group
- Delete the existing rolebinding: kubectl -n devops delete rolebinding devops-rolebinding
- Create: kubectl create rolebinding devops-rolebinding --role=devops --group=devops --namespace devops
- kubectl -n devops get role devops -o yaml
Next time, when you create a new user We need to just follow the authentication steps and we can ignore the authorization process. This will automatically add the new user to devops group and provide access to devops namespace.
D) Avoid giving --kubeconfig=john.kubeconfig
Login as john, and perform the following command
- cd /tmp/rbac
- mkdir -p $HOME/.kube
- cp john.crt $HOME/.kube
- cp john.kubeconfig $HOME/.kube/config
- cp john.key $HOME/.kube
- kubectl get pods # Not required to give
For James,
- cd /tmp/rbac
- mkdir -p $HOME/.kube
- cp james.crt $HOME/.kube
- cp james.kubeconfig $HOME/.kube/config
- cp james.key $HOME/.kube
- kubectl get pods # Not required to give
E) Cleanup
sudo as admin user, in my case it is going be a jenkins users
- kubectl config unset users.john
- kubectl config unset contexts.john
- kubectl config unset users.james
- kubectl config unset contexts.james
- kubectl -n devops delete rolebinding devops-rolebinding
- kubectl delete role devops -n devops
- kubectl delete clusterrole devops
- kubectl delete clusterrolebinding devops
- sudo userdel -f john
- sudo userdel -f james
- rm -rf /home/john
- rm -rf /home/james
C) Authorization - Clusterrole and Clusterrole Binding
- kubectl create clusterrole devops --verb=get,list,watch --resource=pods
- kubectl create clusterrolebinding devops --clusterrole=devops --user=john --group=devops